
We build a global community, bound by a passion for solving security problems such as vulnerabilities. We find owners and disclose to prevent incidents, making the world more secure. We love the internet and aim to understand its weaknesses. We love personal growth, and help our community to grow as individuals and as a group. We are non-partisan, a-political, inclusive and open. We maintain a sense of realism, we’re protective of sensitive data and understand its impact.
Our work consists of 3 major strands:
We run fully funded Bug Bounty programs to help charities and NGOs find and fix vulnerabilities in their infrastructure. This entails a few stages:
To nominate your organisation as a beneficiary please contact our Bug Bounty team.
We have a team of skilled Exploit Researchers who look for previously unknown vulnerabilities (zero-days) in public infrastructure so they can be responsibly reported and fixed, leaving the community safer.
We have 3 tiers of researchers with a mentoring and training system to reduce the global shortage of skilled Cyber practitioners. See our current and former cases
For more info, see our Opportunities.
We have a team of experienced incident responders who can:
To find out more, please see our Opportunities or contact the IR team.
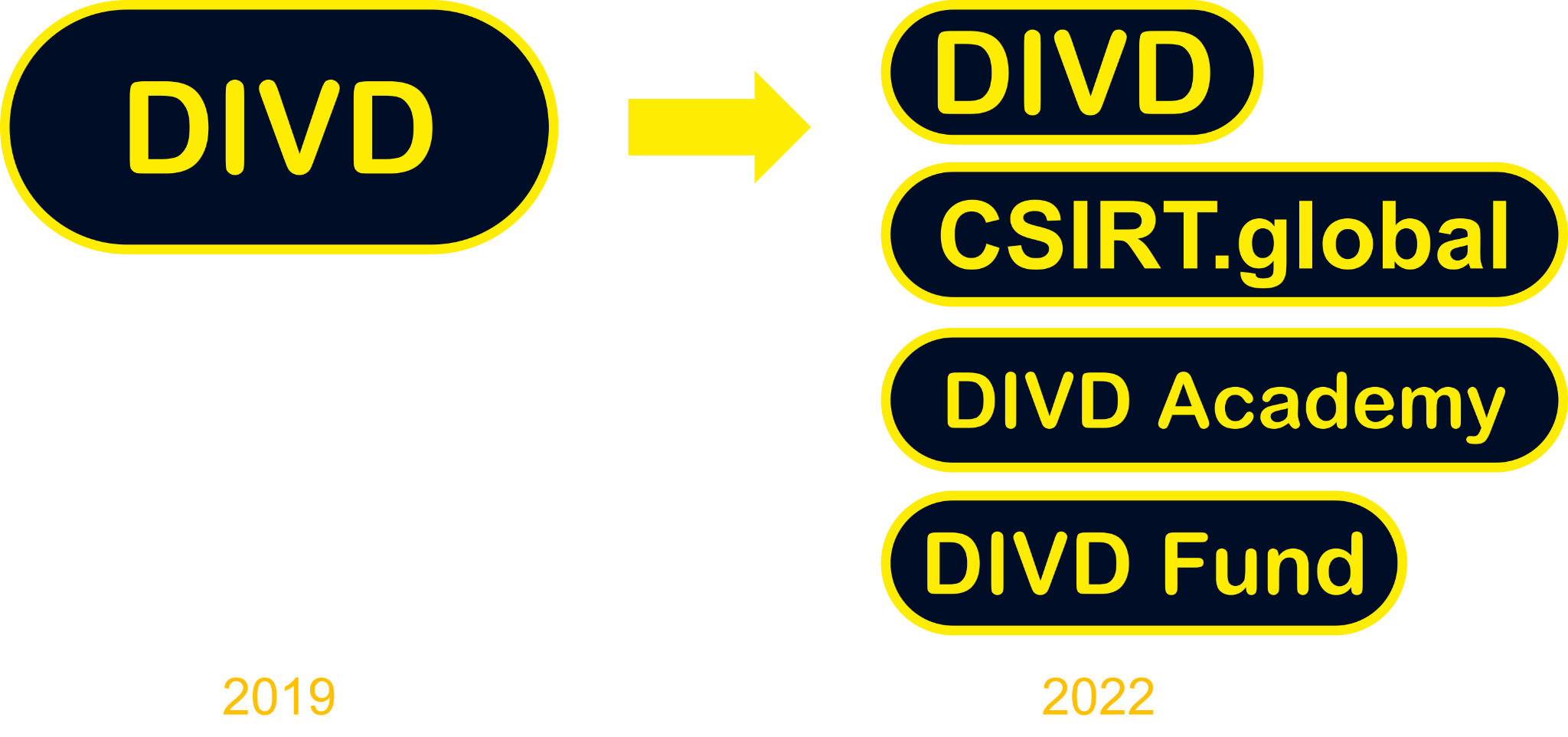
CSIRT.global is a global, volunteer-led, not-for-profit organization, aiming to make the world more secure by going after vulnerabilities no-one else cares for.
We are a sister organization to the Dutch Institute for Vulnerability Disclosure (DIVD). In 2022, international CSIRT activities were moved to CSIRT.global, as a first step to build an international network of like-minded people.
Due to the importance of our work and the sensitivity of some of the information we work with, CSIRT.global has two levels of oversight.
The supervisory board acts as a “senate”, and can steer important decisions within CSIRT.global. We are incredibly happy these veteran hackers and entrepreneurs share their experience and wisdom with us:
The board steers the direction and makes major decisions impacting the organization. Today, the CSIRT.global board members are the founders. This will change going forward: we believe in periodically freshening the organization. This allows for new insights, and fresh leadership to step up and make a difference.
The management is responsible for day to day operations
All CSIRT.global volunteers adhere to our Code of Conduct:
